Visit our new web shop for more products: stealth-phones.com
 What is IMEI, A5, and GSM Localization?
What is IMEI, A5, and GSM Localization?
The International Mobile Station Equipment Identity or IMEI is a number, usually unique, used by a GSM network to identify valid devices. It is also used by IMEI/IMSI catchers / GSM interceptors in order to identify your phone and performing call interception.
The GSM ciphering algorithm is called A5. It can be supressed (active and semi active GSM interceptors) or broken (passive GSM interceptors) in order to eavesdrop your phone calls and SMS. Also, it can be supressed by GSM carrier due to a warrant.
GSM Localization: referring to how the cell towers which receive a phone's signal may be used to calculate its geophysical location. Same technique is used if instead of cell tower the phone is connected to a GSM interceptor. Invizible interrogation messages (called Ping) will be sent to your phone, in order to calculate its location.
All changes of above identifiers and parameters are instantly detected by XCell Stealth Phones, which will warn you every time when such intrusion attempts are in progress.
XCell Stealth Phone versions
XCell Stealth phones come in five verions.
Special Features Table
| Special Features | XCell Basic |
XCell Advanced | XCell Crypt |
XCell Dynamic IMEI |
XCell Dynamic IMEI v2 |
|---|---|---|---|---|---|
|
GSM Interceptor Proximity Alert
|
Yes | Yes | Yes | Yes | Yes |
| XCell Advanced: Yes XCellCrypt: Yes XCellDynamic IMEI: Yes XCell DynamicIMEI v2: Yes | |||||
|
Call Interception Alert
|
Yes | Yes | Yes | Yes | Yes |
| XCell Advanced: Yes XCellCrypt: Yes XCellDynamic IMEI: Yes XCell DynamicIMEI v2: Yes | |||||
|
Dynamic IMEI
|
Yes | Yes | |||
| XCell Advanced:
XCellCrypt:
XCellDynamic IMEI: Yes XCell DynamicIMEI v2: Yes | |||||
|
A5 Change Alert (No/Change Encryption Alert)
|
Yes | Yes | Yes | Yes | Yes |
| XCell Advanced: Yes XCellCrypt: Yes XCellDynamic IMEI: Yes XCell DynamicIMEI v2: Yes | |||||
|
UnPing (Localization Alert)
|
Yes | ||||
| XCell Advanced:
XCellCrypt:
XCellDynamic IMEI:
XCell DynamicIMEI v2: Yes | |||||
|
Channel Lock (ARFCN Lock)
|
Yes | ||||
|
Show TMSI
|
Yes | ||||
|
Clear Call Log
|
Yes | ||||
|
Voice Call Recording
|
Yes | ||||
|
Hunting Mode
|
Yes | Yes | |||
|
Anti Interception Mode
|
Yes | Yes | |||
|
SMS Encryption
|
Yes | ||||
|
Forensic Bullet-Proof
|
Yes | Yes | Yes | Yes | Yes |
|
Price
|
400 euro | 500 euro | 600 euro | 800 euro | 800 euro |
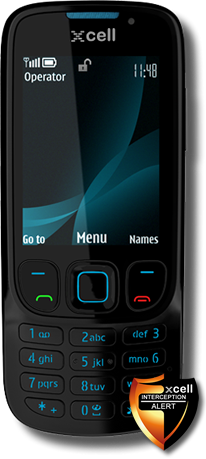 XCell Basic - price: 400 euro
XCell Basic - price: 400 euro
Based on BB5 / Nokia Series 40, 6th Edition, XCell Basic is a customized Nokia 6303i. It warns you about any intrusion or intercepting attempt.
Features:
- GSM Interceptor Proximity Alert. On stand by mode the phone displays a warning icon
 (open lock) in case of monitoring by GSM Interceptor - Call Interception Alert. During the call, the phone will display an icon
(open lock) in case of monitoring by GSM Interceptor - Call Interception Alert. During the call, the phone will display an icon (open lock) in case of active interception.
(open lock) in case of active interception.No sound or vibration alert.
- Forensic Bullet-Proof
The XCell Basic phone cannot be accessed and investigated by forensic software and hardware. Firmware cannot be read/wright or cloned by unlocking boxes.The phone cannot be accessed, read or analysed by any mobile forensic eqipment. Physical extraction and file system extraction is blocked by security filter.
The phone does not need any extra settings. It work as it is.
Important note: The video was filmed in lawful conditions, with the direct support of Special Branch Police Department, with the sole purpose of testing special functions of cell phones. During tests were not intercepted other people mobile phones. XCell Technologies does not own, do not use, do not sell and do not have access to equipment intended for interception of telecommunications.
How does it work?
XCell Basic is capable to detect any changes made by a GSM interceptor on a GSM network, in order to register or attract the phone on the fake network (GSM Interceptor Proximity Alert). Phone registration on a new BTS (the fake BTS generated by a GSM interceptor) is an automated process and this behavior is absolutely common on any cell phone. Any cell phone will automatically choose the most powerful GSM signal, which in case of interception is generated by the GSM interceptor. GSM interceptors (active and semi active ones) force the cell phone handover by suppressing the real network signal with a powerful signal and by mimicking network parameters: MCC, MNC and LAC. But the ARFCN (communication pair channels) and Cell ID are changed in order to force the phone to send registration requests on the "new" BTS. XCell Basic detects these changes and a discrete open lock icon will be displayed on the home screen. Same open discrete lock icon will be displayed on active call, in case of call interception (Call Interception Alert).
-
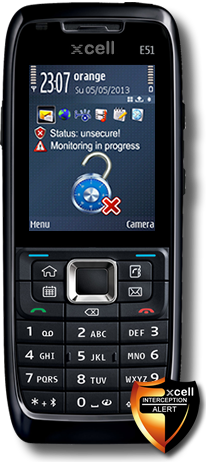 XCell Advanced - price: 500 euro
XCell Advanced - price: 500 euro
Based on S60v3 platform, XCell Advanced runs on the Symbian OS and it is a customized Nokia E51 smartphone.
Features:- GSM Interceptor Proximity Alert. On standby mode the phone will display in case of no threat,the following icons:
 A locked padlock in case of no threat
A locked padlock in case of no threat  Status: secure
Status: secure  Task: network scanning
Task: network scanning When the phone detects an active or semi active GSM Interceptor which scans the surrounding handsets by IMEI or IMSI, the phone status will be changed on Alert Mode and the following icons and messages will be displayed, along with a sound/vibration alert:
 An unlocked padlock in case of GSM interception.
An unlocked padlock in case of GSM interception.  Status: unsecure!
Status: unsecure!  Monitoring (interception) in progress.
Monitoring (interception) in progress.
The phone will react in the same way in case of detecting IMSI catchers.- Call Interception Alert.
 During the call, the phone will display an icon (open lock) in case of active interception.
During the call, the phone will display an icon (open lock) in case of active interception.
Please note that in case of interception carried out by your GSM provider (network operator), the open lock icon will be displayed only during the call.
- Forensic Bullet-ProofThe XCell Advanced Phone cannot be accessed and investigated by forensic software and hardware. Firmware cannot be read/wright or cloned by unlocking boxes. The phone cannot be accessed, read or analysed by any mobile forensic eqipment. Physical extraction and file system extraction is blocked by security filter. The phone does not need any extra settings. It work as it is.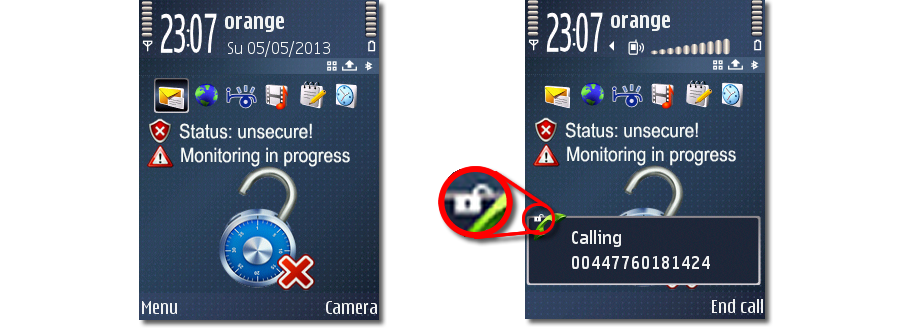
- How does it work?
-
XCell Advanced is capable to detect any changes made by a GSM interceptor on a GSM network, in order to register or attract the phone on the fake network (GSM Interceptor Proximity Alert). Phone registration on a new BTS (the fake BTS generated by a GSM interceptor) is an automated process and this behavior is absolutely common on any cell phone. Any cell phone will automatically choose the most powerful GSM signal, which in case of interception is generated by the GSM interceptor. GSM interceptors (active and semi active ones) force the cell phone handover by suppressing the real network signal with a powerful signal and by mimicking network parameters: MCC, MNC and LAC. But the ARFCN (communication pair channels) and Cell ID are changed in order to force the phone to send registration requests on the "new" BTS. XCell Advanced detects these changes and will warn you: a discrete open lock icon will be displayed on the home screen. Same open discrete lock icon will be displayed on active call, in case of call interception (Call Interception Alert).

Along with the home screen warnings, the phone warns you by sound/vibration alert. -
 XCell Crypt - price: 600 euro
XCell Crypt - price: 600 euro
Based on S60v3 platform, XCell Advanced runs on the Symbian OS and it is a customized Nokia E51 smartphone.
It includes all XCell Advanced features (GSM Interceptor Proximity Alert, Call Interception Alert) plus:
- SMS encryption feature:in case of interception warning you can send encrypted SMS. Please note that the other phone should have the same SMS encryption software installed, for message decryption purposes. Extra encryption applications are provided for 100 euro/application in jad/jar format. Extra encryption applications can be installed on any java enabled phone or Symbian OS.
SMS encryption feature is intended for encryption of outgoing SMS messages. Encryption algorithm is AES-256 and has the function for generating keys from passwords is SHA-256. This is end-to-end encryption, meaning that nobody can read your messages. It can only be read by the recipient who has the right password. And in case you lose your phone no one can read a message, unless you have saved a password in application. But your password will be safe even then because it is saved as hash, not plaintext.
The phone can receive as well encrypted messages for secure communications.
Note: Encryption will work only if both sending and receiving sides install the application.
- Forensic Bullet-ProofThe XCell Crypt Phones cannot be accessed and investigated by forensic software and hardware. Firmware cannot be read/wright or cloned by unlocking boxes.The phone cannot be accessed, read or analysed by any mobile forensic eqipment. Physical extraction and file system extraction is blocked by security filter.
The phone does not need any extra settings. It works as it is.
Important note: The video was filmed in lawful conditions, with the direct support of Special Branch Police Department, with the sole purpose of testing special functions of cell phones. During tests were not intercepted other people mobile phones. XCell Technologies does not own, do not use, do not sell and do not have access to equipment intended for interception of telecommunications.
How does it work?
XCell Crypt is capable to detect any changes made by a GSM interceptor on a GSM network, in order to register or attract the phone on the fake network (GSM Interceptor Proximity Alert). Phone registration on a new BTS (the fake BTS generated by a GSM interceptor) is an automated process and this behavior is absolutely common on any cell phone. Any cell phone will automatically choose the most powerful GSM signal, which in case of interception is generated by the GSM interceptor. GSM interceptors (active and semi active ones) force the cell phone handover by suppressing the real network signal with a powerful signal and by mimicking network parameters: MCC, MNC and LAC. But the ARFCN (communication pair channels) and Cell ID are changed in order to force the phone to send registration requests on the "new" BTS. XCell Crypt detects these changes and will warn you: a discrete open lock icon will be displayed on the home screen. Same open discrete lock icon will be displayed on active call, in case of call interception (Call Interception Alert).
Along with the home screen warning display, the phone warns you by sound/vibration alert.
XCell Crypt is enabled with a SMS ciphering software application. In case of Call Interception Alert or GSM Interceptor Proximity Alert you can send encrypted SMS. Please note that the other phone should have the same SMS encryption software installed. Extra encryption applications are provided and can be sold separately just for 100 euro. XCell Dynamic IMEI - price: 800 euro
XCell Dynamic IMEI - price: 800 euro
It includes all XCell Advanced features plus Dynamic IMEI feature, making the phone untraceable and impossible to be intercepted.
XCell Dynamic IMEI phone is built on Samsung G600 platform.
SPECIAL FEATURES:
1. DYNAMIC IMEIDynamic IMEI feature has four options:
A. Random always:The phone IMEI will always vary, when it is requested by the GSM network or GSM Interceptor. IMEI will be changed on every call or SMS as well.
B. Random on first request:Phone IMEI will be changed when the SIM card is inserted the first time, and when the GSM network requests phone details for registration. In this mode the phone IMEI varies only once after device registration on the network. Further on for all inquiries IMEI sent by the network, phone will give out in a network this IMEI.C. User define:Phone IMEI can be manually defined by the user.
D. Stay original:Phone IMEI always remains original.
2. GSM Interceptor Proximity Alert
 The phone will display an open lock icon and warn you by sound alarm and vibration.
The phone will display an open lock icon and warn you by sound alarm and vibration.Same warning icon will be displayed in case of inteception carried out by your GSM provider (network operator).
3. Call Interception Alert
 During the call, the phone will display an open lock icon. The icon means your calls and messages are not anymore protected by GSM A5/1 encryption as usual and your phone is subject to an active interception.
During the call, the phone will display an open lock icon. The icon means your calls and messages are not anymore protected by GSM A5/1 encryption as usual and your phone is subject to an active interception.
Please note: On standby mode the phone will display the warning icon because there are no communications to be encrypted by the network. This is a normal behaviour.
On standby mode the phone will display the warning icon because there are no communications to be encrypted by the network. This is a normal behaviour. During the call or SMS sending/receiving, there will be displayed a green lock icon which means that A5/1 encryption is provided by the GSM network and your communications are not intercepted. If icon remains red, that means your phone is subject to an active interception performed by a GSM Interceptor or by your GSM provider.
During the call or SMS sending/receiving, there will be displayed a green lock icon which means that A5/1 encryption is provided by the GSM network and your communications are not intercepted. If icon remains red, that means your phone is subject to an active interception performed by a GSM Interceptor or by your GSM provider. If XCell Dynamic IMEI phone is intercepted by a GSM Interceptor, by lowering the encryption level from the stronger A5/1 to the weaker A5/2 (which can be easily and quickly decrypted in real time), then a warning yellow lock is displayed.
If XCell Dynamic IMEI phone is intercepted by a GSM Interceptor, by lowering the encryption level from the stronger A5/1 to the weaker A5/2 (which can be easily and quickly decrypted in real time), then a warning yellow lock is displayed. In case your XCell Dynamic IMEI phone is registered on a GSM network that provides the weaker encryption algorithm A5/2 (China, India etc.), the phone will display a yellow lock icon.
In case your XCell Dynamic IMEI phone is registered on a GSM network that provides the weaker encryption algorithm A5/2 (China, India etc.), the phone will display a yellow lock icon.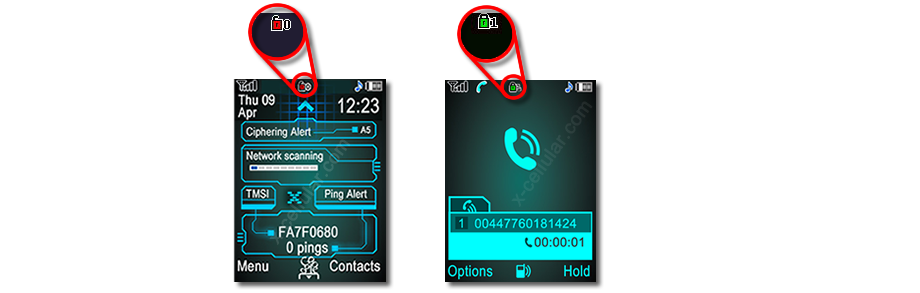
All warning icons will be displayed along with sound/message/vibration alert.
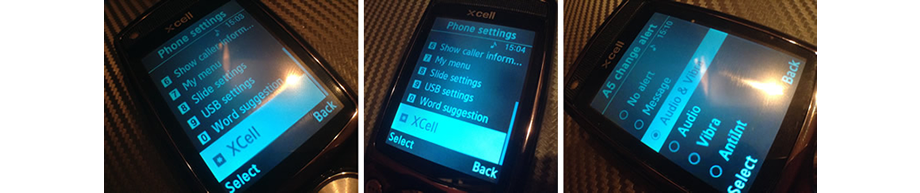
Please note that no calls can be made as long as the phone is under surveillance and no SMS can be sent, as active security measurse. In case you still want to make and receive calls and send/receive messages, please change the phone settings as folowing: Extra Menu > enter password > A5 tracer > A5 change alert > uncheck HandOff option by checking any other alerting option. Conversation automatically breaks in case of phone interception and HandOff option is checked.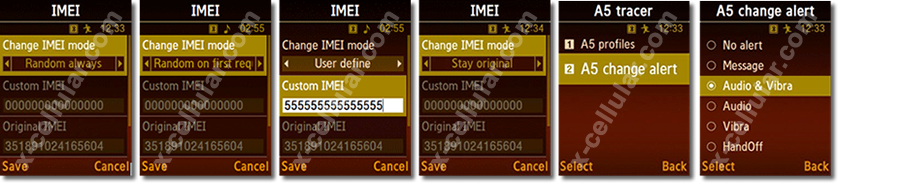
-
- Forensic Bullet-ProofXCell Dynamic IMEI phones cannot be accessed, read or analysed by any mobile forensic equipment. Physical extraction and file system extraction is blocked by security filter.
Important note: The video was filmed in lawful conditions, with the direct support of Special Branch Police Department, with the sole purpose of testing special functions of cell phones. During tests were not intercepted other people mobile phones. XCell Technologies does not own, do not use, do not sell and do not have access to equipment intended for interception of telecommunications.
How does it work?
XCell Dynamic IMEI is capable to detect any changes made by a GSM interceptor on a GSM network, in order to register or attract the phone on the fake network (GSM Interceptor Proximity Alert). Phone registration on a new BTS (the fake BTS generated by a GSM interceptor) is an automated process and this behavior is absolutely common on any cell phone. Any cell phone will automatically choose the most powerful GSM signal, which in case of interception is generated by the GSM interceptor. GSM interceptors (active and semi active ones) force the cell phone handover by suppressing the real network signal with a powerful signal and by mimicking network parameters: MCC, MNC and LAC. But the ARFCN (communication pair channels) and Cell ID are changed in order to force the phone to send registration requests on the "new" BTS. XCell Dynamic IMEI detect these changes and will warn you: a discrete open lock icon will be displayed on the home screen. Same open discrete lock icon will be displayed on active call, in case of call interception (Call Interception Alert).
Along with the home screen warning display, the phone warns you by sound/vibration alert.
If the network characteristics change i.e. using a GSM interceptor or IMSI catcher, or any method to try and trick the SIM into changing to a breakable A5/2 encryption, the phone will detect this and alert the user via an alarm, vibration or display a screen message. No calls or SMS's can then be made.
The handset will also randomly change the IMEI on each call, or you may specify an IMEI. A good way to confirm the handset does change the IMEI and not just gives the appearance of a different IMEI is to assign a known blocked or stolen IMEI to the handset.
Dynamic IMEI feature:
Dynamic IMEI feature is intended for protection of conversations against the control and interception through a GSM interceptor.In order to intercept your phone the GSM interceptor uses the folowing identifiers:
Your phone number (off air it is not transferred, but the operator knows it);
IMSI — unique SIM registration number;
IMEI — unique phone registration number, other than phone number which is contained by SIM.If you change IMEI and insert a new bought SIM (a pre pay one), then all phone identifiers vary. Therefore the operator does not know whom it is necessary to put on the surveillance.
If you have changed only SIM or only have changed IMEI, this will give you nothing and you will continue to be monitorised, as though you changed nothing.
If you simultaneously change IMEI and SIM, that will allow you to avoid any GSM interception. As all your phone identifiers have changed (which has been registered previously into the target selection list of a GSM interceptor), the GSM interceptor operator needs to make additional efforts in order to receive and register your new identifiers. Besides, the system operator cannot understand that he has lost the control over your phone.
A5 tracer feature
This feature is intended for phone protection against the interception performed with active and semi active GSM interceptors.
The active interception systems emulate base station (BTS) and force phones to work not through the real base station, but through this equipment — a false base station. Mobile phones cannot distinguish between a false BTS (a GSM interceptor) and a real one. They choose to register on a BTS only by power level. As long as a GSM interceptor has the strongest signal on a certain area, then all mobile phones within the area will register on that false BTS emulated by the interceptor.
The false base station can:
- switch off A5/1 ciphering algorithm;
- lower ciphering algorithm to weaker A5/2 one;
- not change ciphering (fully passive GSM interceptors).The most widespread interception systems are the ones which lower ciphering level from A5/1 to A5/2 on a constant basis, or just for a period of time needed for calculation of a Session Key (Kc) and Ciphering Key (Ki) that are stored on the SIM.
XCell Stealth Phones can detect ANY active, semi active and passive GSM interceptors, it does not matter the type, the manufacturer or the other technical characteristics.
The phone can be used in two modes: Hunting mode and Anti Interception mode.
1. On Hunting mode:
XCell Dynamic IMEI v2 is the only phone that can actually hunt GSM interceptors, by detecting them in real time. On Hunter mode the phone user will get alerts whenever the phone is intercepted by active, semi active and passive interceptors, or even with the help of GSM operator. Hence, the phone user can fill out any story based on art of deception, can lead counterintelligence special operations, can simply remain silent or even switch off the phone.
For Hunting mode operation please go to Extra menu > enter password > A5 tracer > A5 change alert > uncheck HandOff option by checking any other alerting option. Otherwise, phone conversation automatically breaks in case of phone interception and HandOff option is checked.
2. On Anti Interception mode:
Once the phone get intercepted by any means (GSM interceptors or carrier), any incoming or outgoing call and SMS will be automatically blocked until the threat is over. For Anti Interception mode operation please go to Extra menu > enter password > A5 tracer > A5 change alert > check HandOff option. From now on, phone conversation automatically breaks in case of phone interception. - XCell Dynamic IMEI + ANTI INTERCEPTION (v2) - price:
1000 euro800 euro
It includes all XCell Dynamic IMEI features plus UnPing, Channel lock, Show TMSI, Clear call log and Recording featurs, making the phone the best in branch, untraceable and impossible to be intercepted.
XCell Dynamic IMEI phone is built on Samsung G600 platform.
SPECIAL FEATURES:
1. Dynamic IMEI
2. A5 tracer (GSM Interceptor Proximity Alert and Call Interception Alert)
3. UnPing
4. Channel lock
5. Show TMSI
6. Clear call log
7. Recording
1. Dynamic IMEI
Dynamic IMEI feature has four options:
A. Random always:
The phone IMEI will always vary, when it is requested by the GSM network or GSM Interceptor. IMEI will be changed on every call or SMS as well.
B. Random on first request:
Phone IMEI will be changed when the SIM card is inserted the first time, and when the GSM network requests phone details for registration. In this mode the phone IMEI varies only once after device registration on the network. Further on for all inquiries IMEI sent by the network, phone will give out in a network this IMEI.
C. User defined:
Phone IMEI can be manually defined by the user.
D. Stay original: Phone IMEI always remains original.
Dynamic IMEI feature is intended for protection of conversations against the control and interception through a GSM interceptor.
In order to intercept your phone the GSM interceptor uses the folowing identifiers:
Your phone number (off air it is not transferred, but the operator knows it);
IMSI — unique SIM registration number;
IMEI — unique phone registration number, other than phone number which is contained by SIM.
If you change IMEI and insert a new bought SIM (a pre pay one), then all phone identifiers vary. Therefore the operator does not know whom it is necessary to put on the surveillance. If you have changed only SIM or only have changed IMEI, this will give you nothing and you will continue to be monitorised, as though you changed nothing.
If you simultaneously change IMEI and SIM, that will allow you to avoid any GSM interception. As all your phone identifiers have changed (which has been registered previously into the target selection list of a GSM interceptor), the GSM interceptor operator needs to make additional efforts in order to receive and register your new identifiers. Besides, the system operator cannot understand that he has lost the control over your phone.
2. A5 tracer feature
This feature is intended for phone protection against the interception performed with active and semi active GSM interceptors.
The active interception systems emulate base station (BTS) and force phones to work not through the real base station, but through this equipment — a false base station. Mobile phones cannot distinguish between a false BTS (a GSM interceptor) and a real one. They choose to register on a BTS only by power level. As long as a GSM interceptor has the strongest signal on a certain area, then all mobile phones within the area will register on that false BTS emulated by the interceptor.
The false base station can:
- switch off A5/1 ciphering algorithm;
- lower ciphering algorithm to weaker A5/2 one;
- not change ciphering (fully passive GSM interceptors).
The most widespread interception systems are the ones which lower ciphering level from A5/1 to A5/2 on a constant basis, or just for a period of time needed for calculation of a Session Key (Kc) and Ciphering Key (Ki) that are stored on the SIM.
XCell Stealth Phones can detect ANY active, semi active and passive GSM interceptors, it does not matter the type, the manufacturer or the other technical characteristics.
2.1 GSM Interceptor Proximity Alert The phone will display an open lock icon and warn you by sound alarm and vibration. Same warning icon will be displayed in case of inteception carried out by your GSM provider (network operator).
The phone will display an open lock icon and warn you by sound alarm and vibration. Same warning icon will be displayed in case of inteception carried out by your GSM provider (network operator).
2.2 Call Interception Alert During the call, the phone will display an open lock icon. The icon means your calls and messages are not anymore protected by GSM A5/1 encryption as usual and your phone is subject to an active interception.
During the call, the phone will display an open lock icon. The icon means your calls and messages are not anymore protected by GSM A5/1 encryption as usual and your phone is subject to an active interception.
Please note: On standby mode the phone will display the warning icon because there are no communications to be encrypted by the network. This is a normal behaviour.
On standby mode the phone will display the warning icon because there are no communications to be encrypted by the network. This is a normal behaviour. During the call or SMS sending/receiving, there will be displayed a green lock icon which means that A5/1 encryption is provided by the GSM network and your communications are not intercepted. If icon remains red, that means your phone is subject to an active interception performed by a GSM Interceptor or by your GSM provider.
During the call or SMS sending/receiving, there will be displayed a green lock icon which means that A5/1 encryption is provided by the GSM network and your communications are not intercepted. If icon remains red, that means your phone is subject to an active interception performed by a GSM Interceptor or by your GSM provider. If XCell Dynamic IMEI v2 phone is intercepted by a GSM Interceptor, by lowering the encryption level from the stronger A5/1 to the weaker A5/2 (which can be easily and quickly decrypted in real time), then a warning yellow lock is displayed.
If XCell Dynamic IMEI v2 phone is intercepted by a GSM Interceptor, by lowering the encryption level from the stronger A5/1 to the weaker A5/2 (which can be easily and quickly decrypted in real time), then a warning yellow lock is displayed. In case your XCell Dynamic IMEI phone is registered on a GSM network that provides the weaker encryption algorithm A5/2 (China, India etc.), the phone will display a yellow lock icon.
In case your XCell Dynamic IMEI phone is registered on a GSM network that provides the weaker encryption algorithm A5/2 (China, India etc.), the phone will display a yellow lock icon.
All warning icons will be displayed along with sound/message/vibration alert. 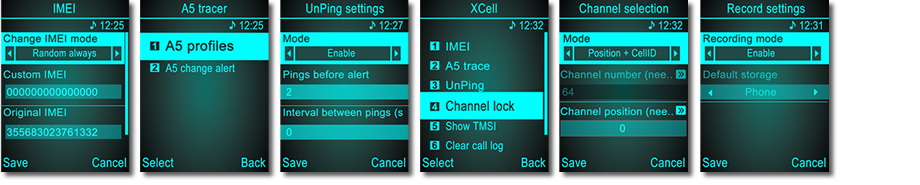
-
3. UnPing
This feature is used to alert you to an abnormal number of GSM network re-registration requests. GSM Interceptors or GSM networks may request this at a higher rate in order to attempt to triangulate your mobile phone for location purposes or for requesting additional identity information from your handset. If a ping is detected coming from the network or from a GSM interceptor based on the associated variables, then the user will be alerted.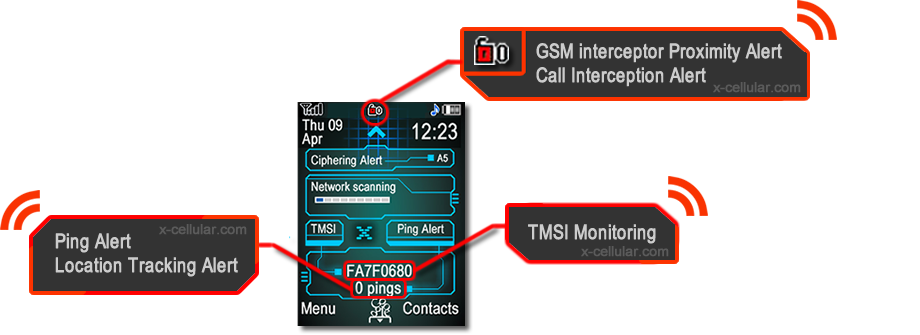
4. Channel lock
This will allow you to lock the phone to a specific GSM channel number (called ARFCN, see Glossary below) within your area. A GSM interceptor will have the strongest signal so as to encourage the phone to register onto it. Please note that if you are not stationary or are travelling then you will obviously lose GSM network coverage when moving around due to the channel numbers being different for each area. If the channel number(s) does not change then this could be an indication of your phone being registered onto a GSM interceptor.
5. Show TMSI
This is the temporary identification which the GSM network allocates to the mobile phone and will change when either the phone is switched off/on or if the phone loses complete network reception. This may remain the same or be limited to a set number of TMSI's whenever the phone is connected/register onto a GSM interceptor.
6. Clear call log
This includes all logs such as outgoing/incoming call details which can be beneficial if for instance the phones happens to get into the wrong hands. This will enable the automatic deletion of all call logs, after each call.
7. Call Recording
All incoming and outgoing call audio will be automatically recorded without emitting any background beeps so as not to arouse any suspicion to the 3rd party. This can be useful for evidential proof of any crucial/important conversations. All recorded files are protected by the phones inbuilt unique 8 digit password security and can be re-played directly from the phone. -
Forensic Bullet-Proof - The XCell Dynamic IMEI v2 Phones cannot be accessed and investigated by forensic software and hardware. Firmware cannot be read/wright or cloned by unlocking boxes.
The phone cannot be accessed, read or analysed by any mobile forensic equipment. Physical extraction and file system extraction is blocked by security filter. - How does it work?
XCell Dynamic IMEI v2 is capable to detect any changes made by a GSM interceptor on a GSM network, in order to register or attract the phone on the fake network (GSM Interceptor Proximity Alert). Phone registration on a new BTS (the fake BTS generated by a GSM interceptor) is an automated process and this behavior is absolutely common on any cell phone. Any cell phone will automatically choose the most powerful GSM signal, which in case of interception is generated by the GSM interceptor. GSM interceptors (active and semi active ones) force the cell phone handover by suppressing the real network signal with a powerful signal and by mimicking network parameters: MCC, MNC and LAC. But the ARFCN (communication pair channels) and Cell ID are changed in order to force the phone to send registration requests on the "new" BTS. XCell Dynamic IMEI detect these changes and will warn you: a discrete open lock icon will be displayed on the home screen. Same open discrete lock icon will be displayed on active call, in case of call interception (Call Interception Alert).
Along with the home screen warning display, the phone warns you by sound/vibration alert.
If the network characteristics change i.e. using a GSM interceptor or IMSI catcher, or any method to try and trick the SIM into changing to a breakable A5/2 encryption, the phone will detect this and alert the user via an alarm, vibration or display a screen message. No calls or SMS's can then be made.
The handset will also randomly change the IMEI on each call, or you may specify an IMEI. A good way to confirm the handset does change the IMEI and not just gives the appearance of a different IMEI is to assign a known blocked or stolen IMEI to the handset.
Also, the phone will alert you when receiving an abnormal number of GSM network re-registration requests (UnPing feature), coming from network itself or from a GSM interceptor which is trying to locate the cell phone or is running a Kc extraction (communications ciphering key) from your SIM card. The phone can be locked to a specific GSM channel number (ARFCN), in order to avoid BCCH manipulations procedures performed by GSM interceptors. XCell Dynamic IMEI v2 will show on home screen the TMSI value, which will remain the same in case of phone interception. The phone will delete automatically the call log after each outgoing or incoming call and all incoming and outgoing call audio will be automatically recorded without emitting any background beeps. All recorded files can be re-played directly from the phone.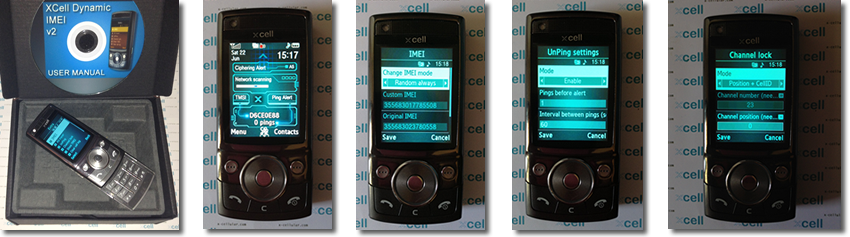
The phone can be used in two modes: Hunting mode and Anti Interception mode.
1. Hunting mode:
XCell Dynamic IMEI v2 is the only phone that can actually hunt GSM interceptors, by detecting them in real time. On Hunting mode the phone user will get alerts whenever the phone is intercepted by active, semi active and passive interceptors, or even with the help of GSM operator. Hence, the phone user can fill out any story based on art of deception, can lead counterintelligence special operations, can simply remain silent or even switch off the phone.
For Hunting mode operation please go to Extra menu > enter password > A5 tracer > A5 change alert > uncheck HandOff option by checking any other alerting option. Otherwise, phone conversation automatically breaks in case of phone interception and HandOff option is checked.
2. Anti Interception mode:
Once the phone get intercepted by any means (GSM interceptors or carrier), any incoming or outgoing call and SMS will be automatically blocked until the threat is over. For Anti Interception mode operation please go to Extra menu > enter password > A5 tracer > A5 change alert > check HandOff option. From now on, phone conversation automatically breaks in case of phone interception.
Important note: The video was filmed in lawful conditions, with the direct support of Special Branch Police Department, with the sole purpose of testing special functions of cell phones. During tests were not intercepted other people mobile phones. XCell Technologies does not own, do not use, do not sell and do not have access to equipment intended for interception of telecommunications.

Please note that no calls can be made as long as the phone is under surveillance and no SMS can be sent, as active security measurse. In case you still want to make and receive calls and send/receive messages, please change the phone settings as folowing: Extra Menu > enter password > A5 tracer >; A5 change alert > uncheck HandOff option by checking any other alerting option. Conversation automatically breaks in case of phone interception and HandOff option is checked.
Important note: The video was filmed in lawful conditions, with the direct support of Special Branch Police Department, with the sole purpose of testing special functions of cell phones. During tests were not intercepted other people mobile phones. XCell Technologies does not own, do not use, do not sell and do not have access to equipment intended for interception of telecommunications.
A5/0, A5/1, A5/2, A5/3
The GSM ciphering algorithm is called A5. There are four variants of A5 in GSM, only first three of which are widely deployed:
A5/0: no ciphering at all
A5/1: strong(er) ciphering, intended for use in North America and Europe
A5/2: weak ciphering, intended for use in other parts of the world, but now deprecated by the GSMA
A5/3: even stronger ciphering with open design
A5/1
Is a stream cipher used to provide over-the-air communication privacy in the GSM cellular telephone standard. It was initially kept secret, but became public knowledge through leaks and reverse engineering. A number of serious weaknesses in the cipher have been identified. A5/1 is used in Europe and the United States.
A5/2
Is a stream cipher used to provide voice privacy in the GSM cellular telephone protocol. A5/2 was a deliberate weakening of the algorithm for certain export regions. The cipher is based around a combination of four linear feedback shift registers with irregular clocking and a non-linear combiner.
ARFCN
In GSM cellular networks, an absolute radio-frequency channel number (ARFCN) is a code that specifies a pair of physical radio carriers used for transmission and reception in a land mobile radio system, one for the uplink signal and one for the downlink signal. This network parameter is used to force the cell phones to send registration requests to a false BTS (IMEI/IMSI catcher).
Authentication Key (Ki)
The authentication key or Ki is a 128 bit key used in the authentication and cipher key generation process. In a nutshell, the key is used to authenticate the SIM on the GSM network. Each SIM contains this key which is assigned to it by the operator during the personalization process. The SIM card is specially designed so the Ki can't be compromised using a smart-card interface.
Ciphering Key (Kc)
The SIM contains the ciphering key generating algorithm (A8) which is used to produce the 64-bit ciphering key (Kc). The ciphering key is computed by applying the same random number (RAND) used in the authentication process to the ciphering key generating algorithm (A8) with the individual subscriber authentication key (Ki). The ciphering key (Kc) is used to encrypt and decrypt the data between the MS and BS. However, a passive GSM interceptor can extract and calculate remotely the Ciphering Key and using it for deciphering in real time.
BCCH
A broadcast control channel (BCCH) is a point to multipoint, unidirectional (downlink) channel used in the Um interface of the GSM cellular standard. The BCCH carries a repeating pattern of system information messages that describe the identity, configuration and available features of the base transceiver station (BTS).
BCCH manipulation
A special technique. GSM interceptors (IMEI/IMSI catchers) uses BCCH manipulation to give a "virtual power" effect of up to several hundred watts. By doing that, a GSM interceptor will trick the handsets, which will always choose the "BTS" with the strongest signal. As well, by changing Cell ID (all other network parameters remains the same - MCC, MNC, LAC) and ARFCN, the interceptor is forcing the cell phones within the area to send registration requests, collecting this way phones identifiers: IMSI, IMEI, classmark, etc.
BTS
The base transceiver station contains the equipment for transmitting and receiving radio signals (transceivers), antennas, and equipment for encrypting and decrypting communications with the base station controller (BSC).
Carrier
A company that provides GSM telecommunications services.
Cell
In personal communications systems (cellular mobile phone systems) a cell is the geographic area served by a single base station. Cells are arranged so that base-station frequencies can be reused between cells. The area surrounding a cell site. The area in which calls are handled by a particular cell site.
Cell ID
A GSM Cell ID (CID) is a generally unique number used to identify each Base transceiver station (BTS) or sector of a BTS within a Location area code (LAC) if not within a GSM network. In some cases the last digit of CID represents cells' Sector ID. This network parameter is used in so called BCCH manipulation by GSM interceptors. By changing Cell ID (all other network parameters remains the same - MCC, MNC, LAC) and ARFCN, the system is forcing the cell phones within the area to send registration requests, collecting this way phones identifiers: IMSI, IMEI, classmark, etc.
Cell Site
The transmission and reception equipment, including the base station antenna, that connects a cellular phone to the network.
Channel Coding
Channel coding is the technique of protecting message signals from signal impairments by adding redundancy to the message signal.
Fade
A fade is a slow change in signal strength.
GSM 1800
The GSM 1800 band provides for a GSM uplink in the range 1710-1785 MHz, a a GSM downlink in the range 1805-1880 MHz.
GSM 1900
The GSM 1800 band provides for a GSM uplink in the range 1850-1910 MHz, a a GSM downlink in the range 1930-1990 MHz.
GSM 900
The GSM 900 band provides for a GSM uplink in the range 890-915 MHz, a a GSM downlink in the range 935-960 MHz.
GSM Air Interface
The GSM air interface operates in the UHF frequency band.
GSM Architecture
A GSM network consists of the mobile station, the base station system, the switching system, and the operation and support system.
GSM Base Station System (BSS) The GSM base station system (BSS) provides the interface between the GSM mobile phone and other parts of the GSM network.
GSM Channels
GSM provides two types of channel: traffic channels and signalling channels
GSM Handover
Handover refers to the process by which a GSM mobile phone's affiliation is transferred from one base station to another.
GSM Interceptor
See IMEI/IMSI catcher.
GSM Security
GSM provides a number of security services, including authentication, key generation, encryption and limited privacy.
IMEI
The International Mobile Station Equipment Identity or IMEI is a number, usually unique, to identify 3GPP (i.e., GSM, UMTS and LTE) and iDEN mobile phones, as well as some satellite phones. The IMEI number is used by a GSM network to identify valid devices and is only used for identifying the device and has no permanent or semi-permanent relation to the subscriber. It is also used by IMEI/IMSI catchers / GSM interceptors in order to identify your phone and performing call interception.
IMSI
The International Mobile Subscriber Identity is a unique identification associated with all cellular networks. It is stored as a 64 bit field and is sent by the phone to the network. It is also used for acquiring other details of the mobile in the home location register (HLR) or as locally copied in the visitor location register. To prevent eavesdroppers identifying and tracking the subscriber on the radio interface, the IMSI is sent as rarely as possible and a randomly generated TMSI is sent instead.
IMSI catcher
Is essentially a false mobile tower acting between the target mobile phone(s) and the service providers real towers. As such it is considered a Man In the Middle (MITM) attack. It is used as an eavesdropping device used for interception and tracking of cellular phones and usually is undetectable for the users of mobile phones. Such a virtual base transceiver station (VBTS) is a device for identifying the International Mobile Subscriber Identity (IMSI) of a nearby GSM mobile phone and intercepting its calls.
The IMSI catcher masquerades as a base station and logs the IMSI numbers of all the mobile stations in the area, as they attempt to attach to the IMSI-catcher. It allows forcing the mobile phone connected to it to use no call encryption (i.e., it is forced into A5/0 mode), making the call data easy to intercept and convert to audio.
LAC
Location Area Code, unique number broadcast by a "base transceiver station" in GSM. A "location area" is a set of base stations that are grouped together to optimise signalling. Typically, tens or even hundreds of base stations share a single Base Station Controller (BSC) in GSM, or a Radio Network Controller (RNC) in UMTS, the intelligence behind the base stations. The BSC handles allocation of radio channels, receives measurements from the mobile phones, controls handovers from base station to base station.
MCC
Mobile country code
, used in wireless telephone network station addressing.
MNC
A mobile network code (MNC) is used in combination with a mobile country code (MCC) (also known as a "MCC / MNC tuple") to uniquely identify a mobile phone operator/carrier using the GSM/LTE, CDMA, iDEN, TETRA and UMTS public land mobile networks and some satellite mobile networks.
MSISDN
Is a number uniquely identifying a subscription in a GSM or a UMTS mobile network. Simply put, it is the telephone number to the SIM card in a mobile/cellular phone. This abbreviation has several interpretations, the most common one being "Mobile Subscriber Integrated Services Digital Network-Number". See also Silent Call.
SIM Card
Smart card that gives GSM phones their user identity. SIM cards make it easy for phones to be rented or borrowed.
Silent Call
In terms of GSM interception, a silent call is a call originated from the GSM interceptor to a specific IMEI/IMSI, in order to make correlations between IMEI/IMSI and MSISDN (Mobile Subscriber Integrated Services Digital Network-Number, which is actually the telephone number to the SIM card in a mobile/cellular phone). By using the silent call, an GSM interceptor can find out a certain phone number alocated to a specific IMEI/IMSI. Silent calls are a result of process known as pinging. This is very similar to an Internet Protocol (IP) ping. A silent call cannot be detected by a phone user. Not to be confused with Spy Call, which mean listen to phone surroundings.
Silent SMS
Many foreign police and intelligence services use clandestine "Silent" SMS to locate suspects or missing persons. This method involves sending an SMS text message to the mobile phone of a suspect, an SMS that goes unnoticed and sends back a signal to the sender of the message.
Also known as Flash-SMS, the Silent SMS uses an invisible return signal, or "ping". Developers from the Silent Services company, who created some of the first software for sending this type of SMS, explain: "The Silent SMS allows the user to send a message to another mobile without the knowledge of the recipient mobile's owner. The message is rejected by the recipient mobile, and leaves no trace. In return, the sender gets a message from a mobile operator confirming that the Silent SMS has been received."
Silent SMS were originally intended to allow operators to ascertain whether a mobile phone is switched on and to "test" the network, without alerting the users. But now, intelligence services and police have found some other uses for the system. Neil Croft, a graduate of the Department of Computer Science at the University of Pretoria in South Africa, explains: "Sending a Silent SMS is like sending a normal SMS, except that the mobile does not see the message it has received. The SMS's information is modified, within the data coding scheme, so that the user who receives the message doesn't notice anything. A Silent SMS can help police to detect a mobile without the person concerned being aware of the request."
Technical bit: in order to tamper with the SMS's information and make it silent, the security services go through a network for sending and receiving SMS known as an SMS gateway, such as the Jataayu SMS gateway. This allows them to interconnect the processing and GSM systems. This method of mass sending appears to be widely used by these security services. In November 2011, Anna Conrad of the Die Linke (The Left) party in Germany, posed a written question (pdf) to her local state assembly concerning the use of Silent SMS by the German police. Her local assembly responded: in 2010, her state conducted 778 investigations and sent 256,000 Silent SMS.
Mathias Monroy, a journalist with Heise Online, argues this surveillance technology is flourishing largely as a result of a legal vacuum: "This is very problematic for privacy, because legally it is unclear whether or not a Silent SMS counts as a communication (…) The state found that it was not one, since there is no content. This is useful, because if it is not a communication, it does not fall under the framework of the inviolability of telecommunications described in Article 10 of the German Constitution."
On December 6, the German Interior Minister Hans-Peter Friedrich announced that German police and intelligence had been sending an average of 440,000 Silent SMS a year since they began using the system. After each SMS was sent, investigators went to the four German mobile operators – Vodafone, E-Plus, O2 and T-Mobile – in order to access the recipient's information. To aggregate this raw data provided by operators, the police use Koyote and rsCase, software supplied by Rola Security Solutions, a company that develops "software solutions for the police".
Silent SMS allow the user to precisely locate a mobile phone by using the GSM network, as Karsten Nohl explains: "We can locate a user by identifying the three antennas closest to his mobile, then triangulating the distance according to the speed it takes for a signal to make a return trip. A mobile phone updates its presence on the network regularly, but when the person moves, the information is not updated immediately. By sending a Silent SMS, the location of the mobile is instantly updated. This is very useful because it allows you to locate someone at a given time, depending on the airwaves."This technique is much more effective than a simple cellular location (Cell ID), as François-Bernard Huyghe, a researcher at IRIS, sets out: "This is the only instantaneous and practical method to track a mobile constantly when it's not in use. We're talking then about geopositioning rather than geolocation. After that, either the police track the information via the operators, or private companies process the data and, for example, refer the investigator to a map where the movements of the monitored phone appear in real time."
The benefits of Silent SMS don't stop there: by sending a large number of these SMS, security services can also disrupt the mobile or remotely reactivate its signal and wear out the battery. A spokesman for the German Interior Ministry tells OWNI: "German police and intelligence services use Silent SMS to reactivate inactive mobile phones and refine the geolocation of a suspect, for example when they move during an interview. The Silent SMS is a valuable investigative tool, which is used only as part of a telecommunications surveillance operation sanctioned by a judge, in a specific case, without violating the fundamental right to protection of privacy."
In France, police and intelligence services work with Deveryware, a "geolocation operator". Deveryware also market a "geolocation employee punchcard", the Geohub, to businesses. Deveryware combine cellular localization, GPS, and other "real-time location" techniques. Questioned by OWNI whether Silent SMS were one of these techniques, the company's response was evasive: "Regretfully we are unable to provide an answer, given the confidentiality imposed on us by legal requisitions." Deveryware's applications enable investigators to map and compile a history of a suspect's movements. Laurent Ysern, head of investigations for SGP Police, states: "All investigative services have access to the Deveryware platform. With this system, one can follow a person without having to be behind them. There's no need for shadowing, so less staff and equipment needs to be mobilized."
While in Germany the Ministry of the Interior responded within 48 hours, the French government remains strangely silent. There has been one single response, from the Press Department of the National Police: "Unfortunately, no one at the PJ (Police Judiciare) or the public safety office is willing to comment on the subject, these are investigative techniques …"Silence too from the French telecoms operators SFR and Bouygues Telecom. Sebastien Crozier, a union delegate at France Telecom-Orange, says: "Operators always collaborate with the police, it's a public service obligation: they act in accordance with judicial requests…There is no definitive method, sending SMS is one of the methods used to geolocate a user. We mainly use this technique to "reactivate" the phone."
By 2013, the use of these surveillance methods is expected to reach an industrial scale. The Department of Justice will set up, with the help of the arms company Thales, a new national platform of judicial interception (PNIJ), which is expected to centralize all legal interception, i.e, phone-tapping, but also summons such as requests for cell location. Sebastien Crozier remarks: "This interface between police officers and operators will streamline court costs and reduce processing costs by half, because until now summons have been handled station by station…There will be more applications, but it will be less expensive for operators like the police." source
When using XCell Stealth phones you can block silent SMS simply by deleting SMS center number, stored on phone memory. Go to Menu > Messages > Settings > Text messages > Sending options > Service center > delete the service center number > press Save > Exit.Please note that by deleting that phone number, you will not be able to send any SMS.
If you want to know if someone is trying to locate you by sending silent SMS, activate UnPing feature and then go to mainmenu > my files > other files > log.txt. All data is date/time/detail stamped. There you can find if someone is trying to locate your phone, when was doing that (time, date) and how many times was trying to locate you.
Spy CallA Spy Call is a call made from a GSM interceptor to a mobile phone, in order to listen to phone surroundings. This call cannot be detected by the phone user.
TMSI
The Temporary Mobile Subscriber Identity (TMSI) is the identity that is most commonly sent between the mobile and the network. TMSI is randomly assigned by the VLR
to every mobile in the area, the moment it is switched on. The number is local to a location area, and so it has to be updated each time the mobile moves to a new geographical area.The network can also change the TMSI of the mobile at any time. And it normally does so, in order to avoid the subscriber from being identified, and tracked by eavesdroppers on the radio interface. This makes it difficult to trace which mobile is which, except briefly, when the mobile is just switched on, or when the data in the mobile becomes invalid for one reason or another. At that point, the global "international mobile subscriber identity" ( IMSI
) must be sent to the network. The IMSI is sent as rarely as possible, to avoid it being identified and tracked.
Triangulation
How does the pinpointing of mobile users work, and just how accurate is it?
There are two methods for pinpointing the location of cell phone users. Cell phones equipped with Global Positioning System (GPS) capability, use signals from satellites to pinpoint location very accurately. The second, and less-accurate method is often called “Cell Tower Triangulation”, referring to how the cell towers which receive a phone’s signal may be used to calculate its geophysical location.According to some industry research estimates, only about 11% of phones manufactured this year will have the GPS capability, so the remaining 89% of phones without GPS would have to depend upon “Cell Tower Triangulation” in order to disclose geolocation data for applications.
Just what is Cell Tower Triangulation?
In a best-case-scenario, a cell phone's signal may be picked up by three or more cell towers, enabling the "triangulation" to work. From a geometric/mathematical standpoint, if you have the distance to an item from each of three distinct points, you can compute the approximate location of that item in relation to the three reference points. This geometric calculation applies in the case of cell phones, since we know the locations of the cell towers which receive the phone's signal, and we can estimate the distance of the phone from each of those antennae towers, based upon the lag time between when the tower sends a ping to the phone and receives the answering ping back.
In many cases, there may actually be more than three cell towers receiving a phone’s signal, allowing for even greater degrees of accuracy (although the term “triangulation” isn’t really correct if you’re using more than three reference points). In densely developed, urban areas, the accuracy of cell phone pinpointing is considered to be very high because there are typically more cell towers with their signal coverage areas overlapping. In cases where a cell user is inside large structures or underground, cell tower triangulation may be the only location pinpointing method since GPS signal may not be available.
For many cell tower networks, the pinpointing accuracy may be even greater, since directional antennae may be used on the tower, and thus the direction of the cell phone’s signal might be identifiable. With the signal direction plus the distance of the phone from the cell tower, accuracy might be pretty good, even with only two towers.
However, there are many places where there are fewer cell towers available, such as in the fringes of the cities and out in the country. If you have fewer than three cell towers available, pinpointing a mobile device can become a lot less precise. In cities where there are a lot more vertical structures which can be barriers to cell phone broadcasting and receiving, there have to be many more cell towers distributed in order to have good service. In the countryside, there are relatively fewer cell towers and a phone's signal may be picked up only by a single one at much greater distance.
Those areas where a phone is only getting picked up by a single tower, and if it's equipped with only omnidirectional antennae, the accuracy becomes even less. In rural areas, coverage of the cell tower can vary from about a quarter of a mile to several miles, depending upon how many obstacles could be blocking the tower's signal.
How extensive is government monitoring?
No civilian is authorised to know. Some governments in the EU, such as the UK government, have laws and practices that allow the government to collect and use intelligence in legal cases without disclosing their sources or methods. Chapter 8 of the Crown Prosecution Service’s Disclosure Manual includes: “the ability of the law enforcement agencies to fight crime by the use of covert human intelligence sources, undercover operations, covert surveillance, etc” and “the protection of secret methods of detecting and fighting crime”.
According estimates made by whistleblower William Binney, a former director of the US NSA’s World Geopolitical and Military Analysis Reporting Group), the US NSA alone has assembled 20 trillion “transactions” − phone calls, emails and other forms of data − just from Americans (April, 2012). Government agencies are not the only organisations interested in the personal data stored on, or transmitted through, your mobile phone. Self-styled cyber criminals are now jumping on the bandwagon to reap benefits previously enjoyed only by government and intelligence agencies.
Target phone location performed by GSM interceptor with target location capabilities.
The method of operation is based on two vehicles. First vehicle with the interception system that forces the target phone to send continues signal transmission. The second vehicle is deployed with the interceptor and location components. The direction to target is displayed as a compass pointer and the relative signal strength is shown as a bar graph and numerically. The audio tone increases in frequency as interceptor gets closer to the target giving a clear warning of a close encounter.
Xcell Dynamic IMEI phones will detect in real time this continuos signal transmission, as an abnormal number of GSM network re-registration requests. When a ping is detected coming from the network or from a GSM interceptor like above, then the user will be alerted.











 Product status: available
Product status: available